WASTON: Inferring Critical Information to Enable Spoofing Attacks using COTS mmWave Radar
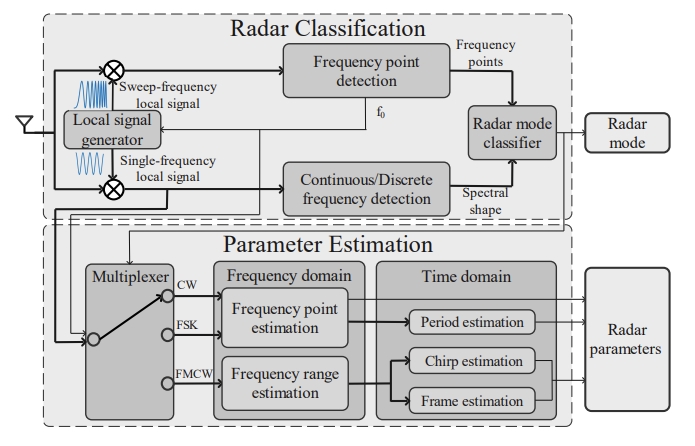
Radar spoofing attacks mislead victim radars by injecting false information. Successful attacks require prior knowledge of the victim radar’s mode and parameters, and existing works obtain this critical information with expensive equipment, e.g., software-defined radio or spectrum analyzer. In this paper, we propose WASTON, a low-cost system for radar mode detection and parameter estimation using commercial off-the-shelf (COTS) mmWave radars. To overcome the disadvantage of low sampling frequency of COTS mmWave radars, we design two special local signals to detect frequency points and spectral shapes for radar mode detection. We propose a novel parameter estimation algorithm to estimate frequency- and time-domain parameters for spoofing different radars. We have implemented a prototype on the TI AWR1843 platform and conducted extensive experiments to evaluate the performance of WASTON. Our experimental results demonstrate that WASTON achieves an accuracy of 100% for mode detection and 99% for parameter estimation. Furthermore, we demonstrate that the estimated parameters can be used to launch a successful spoofing attack against the victim radar.